Cryptocurrency Mining Security Basics for New Miners

Most American first-time cryptocurrency miners are surprised to learn that a single cybersecurity lapse can wipe out months of earnings. As ASIC miners become the powerhouse behind profitable mining in the United States, the stakes are higher than ever. Understanding the unique risks linked to hardware performance, firmware vulnerabilities, and evolving threats is crucial. This guide provides practical tips to help you protect your mining investment and maximize the reliability and profitability of your operation.
Defining Cryptocurrency Mining Security Essentials
Cryptocurrency mining security represents a complex landscape of technical protections designed to safeguard digital assets and computational resources from unauthorized access and potential cyber threats. At its core, mining security involves protecting specialized hardware, network connections, and digital wallets from potential breaches that could compromise mining operations.
The fundamental security framework for cryptocurrency miners encompasses multiple critical layers of defense. Cybersecurity researchers have consistently highlighted the need for comprehensive protection strategies that go beyond traditional network security approaches. These strategies include implementing robust authentication protocols, maintaining updated software environments, and developing sophisticated intrusion detection systems that can identify and neutralize potential mining malware.
Effective mining security requires miners to understand and mitigate several key risk vectors. Unauthorized access remains the primary threat, with potential attackers seeking to hijack mining equipment, steal computational resources, or redirect mining rewards. Preventing malware exploitation demands constant vigilance and proactive system monitoring, including regular software updates, strong password management, and implementing multi-factor authentication for all mining-related accounts and systems.

Pro tip: Invest in a dedicated, isolated network environment for your mining operations to minimize potential security vulnerabilities and reduce the risk of cross-contamination from other networked devices.
Types of Mining Hardware and Unique Risks
Cryptocurrency mining hardware represents a diverse ecosystem of computational devices, each with distinct capabilities and inherent security vulnerabilities. Different mining hardware types expose unique attack surfaces and operational risks, requiring miners to understand the specific security challenges associated with their chosen equipment.
The primary mining hardware categories include Central Processing Units (CPUs), Graphics Processing Units (GPUs), and Application-Specific Integrated Circuits (ASICs). CPUs, the original mining hardware, are now considered least efficient due to low computational power and high energy consumption. GPUs offer more processing capability and flexibility, making them popular among miners seeking adaptable mining solutions. ASICs represent the most specialized and powerful mining hardware, designed exclusively for specific cryptocurrency mining algorithms with maximum computational efficiency.
Comprehensive security analysis reveals that each hardware type presents distinct vulnerabilities that miners must proactively address. ASICs, while most secure due to their specialized design, can still be compromised through physical tampering or firmware vulnerabilities. GPUs face more complex security challenges, including potential malware infiltration and resource hijacking. CPUs remain the most vulnerable, with lower computational barriers making them easier targets for unauthorized mining activities.
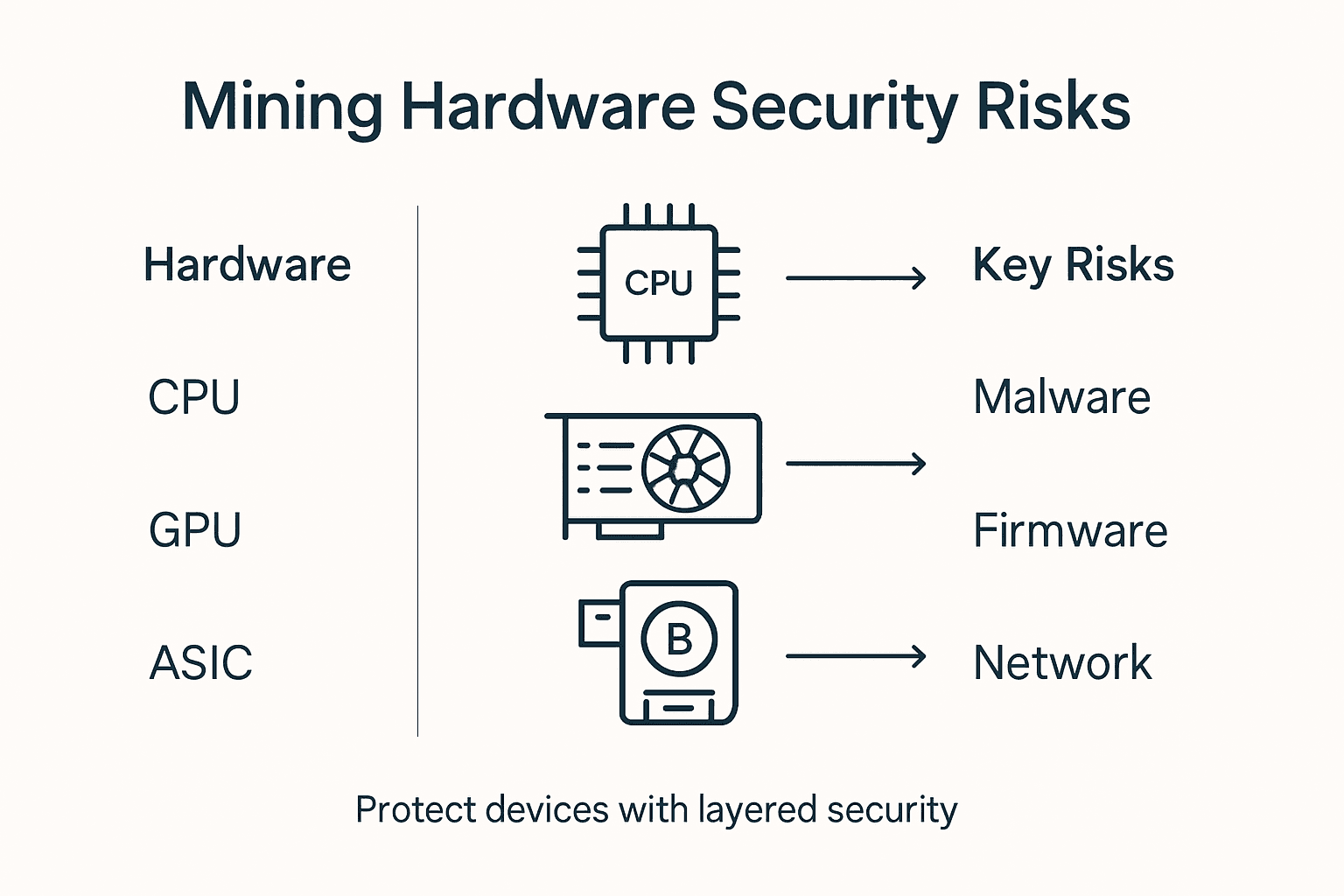
Here’s how popular mining hardware types differ in key security and operational aspects:
| Hardware Type | Common Risks | Security Management | Efficiency Level |
|---|---|---|---|
| CPU | Easy malware exploitation | Frequent patching needed | Low |
| GPU | Malware and resource theft | Isolate and monitor devices | Medium |
| ASIC | Firmware/physical tampering | Secure updates and audits | High |
Pro tip: Invest in hardware from reputable manufacturers with robust firmware update mechanisms and implement regular security audits to identify and mitigate potential hardware-specific vulnerabilities.
How ASIC Miners Impact Security and Profitability
Application-Specific Integrated Circuits (ASICs) have fundamentally transformed cryptocurrency mining by introducing unprecedented computational efficiency and specialized performance. Mining profitability increasingly depends on understanding the complex relationship between ASIC technology and network security dynamics, requiring miners to navigate intricate technological and economic considerations.
The specialized design of ASIC miners provides significant advantages in computational power and energy efficiency compared to traditional mining hardware. These purpose-built devices can perform cryptographic calculations exponentially faster than general-purpose processors, dramatically reducing electricity consumption and increasing potential mining rewards. However, this technological advancement comes with inherent security trade-offs that miners must carefully evaluate and manage.
Advanced security research reveals critical vulnerabilities associated with ASIC mining infrastructure, particularly concerning network centralization risks. The high cost and technical complexity of ASIC hardware create barriers to entry, potentially concentrating mining power among well-resourced participants. This concentration increases the risk of 51% attacks, where a single entity could theoretically control majority computational power, undermining the decentralized principles fundamental to cryptocurrency networks.
Pro tip: Regularly update your ASIC firmware, diversify your mining pools, and maintain robust network segmentation to mitigate potential single-point-of-failure risks in your mining infrastructure.
Legal Compliance for U.S. Mining Operations
Cryptocurrency mining operations in the United States occupy a complex legal landscape that requires careful navigation of federal and state regulatory requirements. Federal regulatory agencies increasingly scrutinize cryptocurrency mining activities to ensure compliance with existing securities and financial regulations, placing significant responsibility on miners to understand and adhere to evolving legal frameworks.
The primary legal considerations for U.S. mining operations center on three critical domains: tax reporting, energy consumption regulations, and potential securities law implications. Miners must register their operations as legitimate business entities, maintain comprehensive financial records, and report cryptocurrency mining income accurately to the Internal Revenue Service (IRS). Additionally, commercial mining operations must comply with local and state electricity usage regulations, which can vary significantly across different jurisdictions.
Institutional guidelines emphasize the importance of cybersecurity and unauthorized usage prevention in cryptocurrency mining contexts, particularly when utilizing institutional or shared computing resources. U.S. miners must implement robust security protocols, obtain necessary permissions for mining activities, and ensure their operations do not inadvertently violate institutional or network usage policies. This includes maintaining clear documentation of mining intent, resource allocation, and comprehensive audit trails to demonstrate compliance and prevent potential legal complications.
Pro tip: Consult with a tax attorney specializing in cryptocurrency regulations to develop a comprehensive compliance strategy that addresses federal, state, and local legal requirements for your specific mining operation.
Cybersecurity Threats Facing Mining Rigs
Cryptocurrency mining operations face an increasingly complex landscape of cybersecurity challenges that demand sophisticated defense strategies. Cloud-based security frameworks highlight multiple critical vulnerabilities targeting mining infrastructure, with sophisticated attackers constantly developing new methods to compromise mining equipment and steal computational resources.
The primary cybersecurity threats to mining rigs include cryptojacking, malware infiltration, and network-based attacks. Cryptojacking represents a particularly insidious risk, where attackers hijack mining hardware to generate cryptocurrency without the owner’s consent, consuming electricity and computational power while reducing overall system performance. Malware specifically designed to target cryptocurrency mining equipment can create backdoors, steal wallet credentials, and redirect mining rewards to unauthorized accounts, potentially causing significant financial damage.
Advanced research indicates widespread vulnerabilities in mining infrastructure security protocols, revealing that many mining operations lack comprehensive defensive measures. Network-level attacks pose substantial risks, including distributed denial-of-service (DDoS) attempts, man-in-the-middle exploits, and sophisticated phishing campaigns designed to compromise mining equipment credentials. These attacks can result in complete operational disruption, financial losses, and potential long-term damage to mining infrastructure.
Use this quick reference to understand and address major mining cybersecurity threats:
| Threat Type | Impact on Miner | Essential Defense |
|---|---|---|
| Cryptojacking | Resource drain, lost payouts | Hardware isolation |
| Malware | Stolen credentials, loss of funds | Regular firmware updates |
| DDoS Attack | Service downtime, lost earnings | Network segmentation |
Pro tip: Implement a multi-layered security approach that includes hardware isolation, regular firmware updates, network segmentation, and comprehensive monitoring to proactively defend against emerging cryptocurrency mining threats.
Avoiding Common Mistakes and Losses
Cryptocurrency mining involves numerous potential pitfalls that can dramatically impact operational effectiveness and financial outcomes. Institutional cybersecurity guidelines highlight critical mistakes that can compromise mining infrastructure and lead to substantial losses, underscoring the importance of proactive risk management and strategic planning.
New miners frequently encounter several fundamental errors that can undermine their mining operations. Unauthorized resource utilization represents a significant risk, where miners inadvertently violate institutional or network usage policies. Equipment selection mistakes, such as purchasing inefficient hardware or failing to calculate true operational costs, can result in negative returns. Additionally, neglecting proper electrical infrastructure and cooling systems can lead to premature hardware failure and reduced mining efficiency.
Comprehensive security research reveals systematic vulnerabilities that inexperienced miners often overlook, including inadequate network protection, poor credential management, and insufficient understanding of mining ecosystem dynamics. Common mistakes include using outdated software, neglecting firmware updates, failing to implement robust authentication mechanisms, and overlooking potential tax and regulatory compliance requirements. These oversights can expose miners to financial risks, potential legal complications, and increased vulnerability to cyber attacks.
Pro tip: Develop a comprehensive risk assessment checklist that covers hardware selection, network security, electrical infrastructure, and regulatory compliance before launching your mining operation.
Secure Your Mining Success with Trusted ASIC Hardware from ING Mining
Cryptocurrency mining security demands more than just technical knowledge it requires reliable hardware and expert guidance to avoid costly mistakes like malware vulnerabilities or inefficient equipment choices. If you are a new miner looking to build a secure and profitable operation ING Mining specializes in sourcing refurbished ASIC miners that undergo rigorous testing and professional inspection. We help you understand critical factors such as miner performance power requirements and long-term operational costs so you can confidently mitigate risks highlighted in the article.
Explore our selection of trusted used miners and benefit from hands-on real-world advice designed to protect your investment and maximize returns. Don’t wait until security threats or legal complexities disrupt your mining. Visit ING Mining today to start building a safer mining operation with equipment and expertise that meet the highest standards.
Frequently Asked Questions
What are the security essentials for cryptocurrency mining?
Effective cryptocurrency mining security includes protecting hardware, network connections, and digital wallets with robust authentication protocols, updated software, and intrusion detection systems.
What types of mining hardware are available and their risks?
Mining hardware types include CPUs, GPUs, and ASICs, each with unique vulnerabilities. CPUs are easy targets for malware, GPUs face malware and resource theft, while ASICs can be compromised via physical tampering or firmware vulnerabilities.
How do ASIC miners affect mining security and profitability?
ASIC miners enhance profitability through increased computational efficiency but pose a security risk due to potential network centralization, which can lead to 51% attacks.
What are common cybersecurity threats to mining operations?
Common cybersecurity threats include cryptojacking, malware infiltration, and network-based attacks, which can drain resources, steal credentials, or disrupt operations.
Recommended
- [Mining 101: A Beginner’s Guide to Cryptocurrency Mining ] | ING MINING™](https://ingmining.com/mining-101-a-beginners-guide-to-cryptocurrency-mining/)
- 5 Tips for Maximizing Your Cryptocurrency Mining Profitability | ING MINING™
- Top Tips for Successful Cryptocurrency Mining | ING MINING™
- Ultimate Beginner’s Guide to Cryptocurrency Mining | ING MINING™